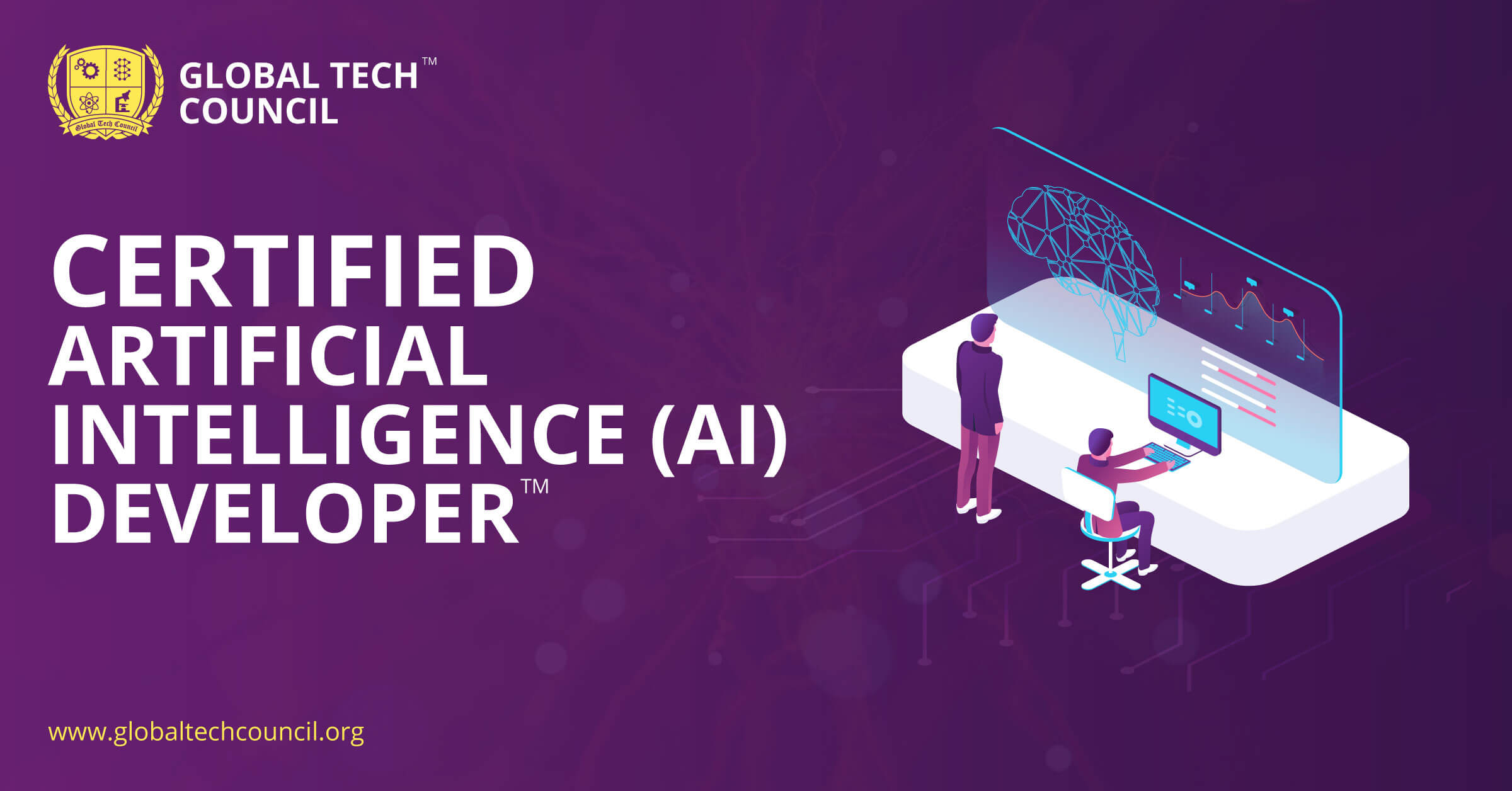
Certified White Hat Hacker™
WhiteHat hackers are also known as Ethical Hackers. WhiteHat hackers are in high demand because they play a critical role in cybersecurity. These experts proactively find weak areas in security networks and fix them before attackers can exploit them.
The Certified WhiteHat Hacker program is by the Global Tech Council. The certification course provides a deeper understanding of security systems, ethical hacking techniques, and security practices that must be followed. Certified ethical hackers work in various fields, including health care, finance, government, and many more. So, if you want to put your programming skills to good use, this may be your gateway to a rewarding career in cybersecurity as an ethical hacker.
- Know what it means to be a WhiteHat Hacker
- Understand various techniques of ethical hacking
- Gain in-depth knowledge about systems, networks, and IoT security
- Learn about various Security best practices
 7 hours
7 hours
 Lifetime
Lifetime
Self-paced
 Online
Online