Wondering what social engineering is? Is the name confusing? In this post, we’ll tell you all about social engineering, social engineering attacks, how to prevent them, and become a better network security engineer.
Learning Of Blog
-
- Introduction
- How Does Social Engineering Work?
- Common Attack Techniques
- How to Prevent Social Engineering Attacks
- Conclusion
Introduction
Everyone is aware of hackers who use their skills and technical expertise to gain access to a system. These attackers are in the headlines all the time and encourage companies to hire professionals with a network security certification and enhance their security systems.
However, there’s one breed of hackers with a different set of tools and methodologies to gain access to a system called social engineers. This term can be confusing as the terms ’social’ and ‘engineering’ are not often heard together. These ‘social engineers’ do not use high-tech methods instead of attack by targeting the human brain. They convince people not to follow the best practices of data security and trick them into giving up sensitive information.
Social engineering is a large tree with a lot of branches under it. In this article, we’ll tell you about the most common methods and how to be safe from them.
How Does Social Engineering Work?
A virus or security breach, in general, depends on the efficiency of the techniques or malicious code to infiltrate a system; social engineering attacks the human brain. If executed well, the infiltrator can quickly gain access to buildings, systems, data, multimedia devices, and internal servers. For example, some criminals prefer to take the road less traveled by. They do not work for several months on a new malware strain, they portray themselves as IT professionals and trick the people into giving up sensitive data like passwords, bank details, SSN, and the like. If the person they are targeting is not alert and falls in their trap, they could gain access to anything they want.
If you’re a business owner or at a senior position, encourage your employees to be aware of such techniques and enroll for network security training courses.
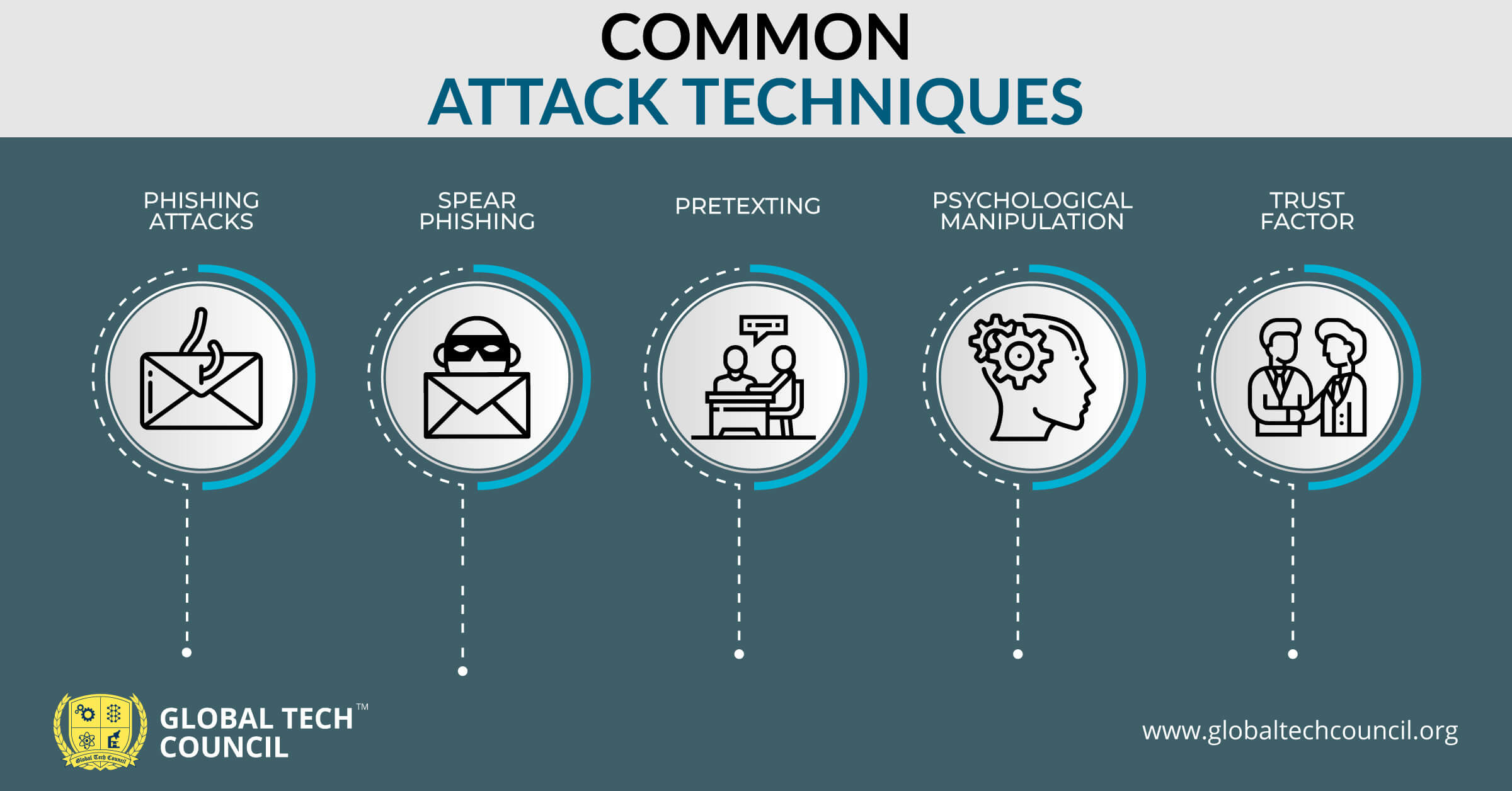
Common Attack Techniques
Attackers use varied techniques to play with the human mind. Some of the most common methods are:
-
Phishing Attacks
This technique focuses on sending emails to a large number of people to reveal personal details such as their password. The emails look like they are from a legitimate source, and some people can easily fall into this trap if they do not read the email carefully.
-
Spear Phishing
Spear phishing is similar to phishing, but the target audience is narrowed down to a specific group of people or an individual. For example, the attacker may ask the finance manager to send a payment to his offshore bank account.
-
Pretexting
Pretexting is the most common form of social engineering attackers follow these days. In this, the attacker pretends to need personal data to confirm the identity of the targeted person. This can be through emails or calls. An everyday example may be an attacker calling a person stating that he is talking on behalf of his bank and may try to reveal personal details to address his query.
-
Psychological Manipulation
While executing a social engineering attack, attackers exploit human emotions such as helpfulness, greed, fear, and obedience. If a person is not able to control his feelings, the attackers will gain access to the information they need (in minutes) and will never be caught.
-
Trust Factor
Do you trust your friends or family members with your personal details? This is precisely why some attackers target you through the email accounts of the people you believe. They’ll send you malicious links through such email accounts, and when you download them, their job is done.
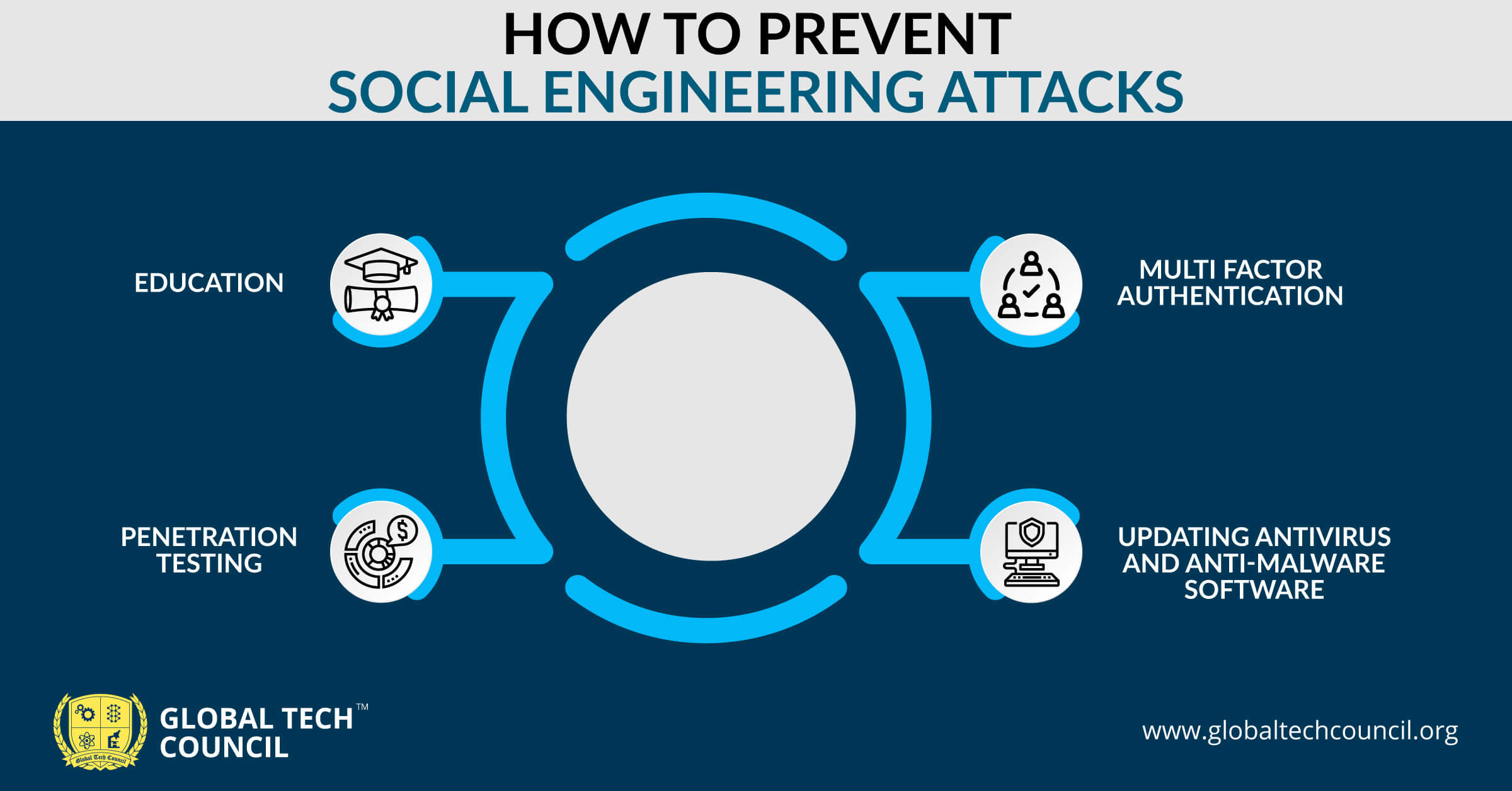
How to Prevent Social Engineering Attacks
Humans form companies, and humans are prone to make wrong decisions because of their emotions. That’s why companies need a social engineering plan to fight against attacks, safeguard their data, and keep their employees out of danger.
How? Read below
- Education – Make sure that your company has a well-documented security policy, and these policies should be taught every employee so that they are aware of social engineering attacks.
- Penetration Testing – If you think that your security guidelines are in place and everyone is aware of them, try testing them. Hire a network security engineer to penetrate your network by following some of the standard practices of social engineering. For example, sending an email from a spoof email id to all the employees will reveal the ground of the implementation of security policies.
- Multi Factor Authentication – Enhancing how your security layers for users to access systems and data can help in avoiding social engineering attacks. Combining passwords with biometrics, for example, is one way that multifactor authentication can beat the criminals at their own game.
- Updating Antivirus and Anti-Malware Software – Regularly update your antivirus and anti-malware. Solid antivirus and anti-malware protection will prevent malicious links and downloads from reaching users’ mailboxes in the first place.
Conclusion
Not everyone in the company is not tech-savvy, especially senior members. There is a possibility that someone from the finance team might not be aware of the ill practices followed by attackers.
But when it comes to social engineering attacks, even a small mistake can prove to be very costly for an organization.
Global Tech Council offers a range of network security engineer certifications for you to help your employees be alert and not compromise your valuable data.
Leave a Reply