We live in a digital era and continuously use the internet for our day to day activities. Cyber-security is considered as one of the critical national security issues of our times. However, there is a global crunch for cybersecurity experts. By developing the required skills through recognized cybersecurity certifications online, one can make use of this huge opportunity.
Learning Of Blog
- What is Cyber Security?
- Cyber Security Process
- What is Threat Modeling?
- Threat Modeling Process
- Benefits of Threat Modeling
- Threat Modeling Methods
- Tools for threat Modeling
- Trends
So if you are an aspiring hacker or concerned about your privacy and security online, then start right away.
WHAT IS CYBERSECURITY?
Cybersecurity is the application of technologies, processes, and controls to protect systems, networks, devices, and data from cyber-attacks. Moreover, it aims to reduce the risk of cyberattacks and protect against the unauthorized exploitation of systems, networks, and technologies. For beginners, it starts with learning concepts of networks and systems.
CYBERSECURITY PROCESS
Any cybersecurity training starts with an understanding of the cybersecurity process. It is much more than just technology. Let us look at each of the components :
- PEOPLE – Users should be aware of their role in reducing and preventing cyber threats. They should be mindful of the risks associated with the same. Secondly, having a dedicated cybersecurity team with the required skills and qualifications is also a necessity for any business.
- PROCESS – The implementation part of any cybersecurity strategy comes under this phase. Continuous review of the processes is necessary as cybersecurity threats are very dynamic in nature.
- TECHNOLOGY – The data collected must follow the CIA triad i.e.
- Confidentiality: Ensuring this will organize the information in terms of authorization and access.
- Integrity: During data transfers, this will ensure that no unauthorized modifications take place.
- “>Availability: Critical systems must be immune to cyber threats, hardware failures, or any other event that might affect availability.
WHAT IS THREAT MODELLING?
Threat modeling is a process to identify, address, and assess any potential threats or vulnerabilities of a system. In threat modeling, we identify the valuable assets that an organization wants to protect, then the assets are prioritized according to the vulnerability and attack vectors associated with them. It is used to generate an abstraction of the system; profiles of the potential adversary, including adversary’s capabilities, goals, methods and motivations; and a list of potential threats that may arise in the future. The motive of threat modeling is to determine where most efforts should be put to keep a system secure.
Three main elements of threat modeling:
1. Assets
2. Vulnerabilities
3. Threats
The organization then brainstorms, ‘Who would want to exploit the vulnerability, and why?’. This leads the cybersecurity expert team to a detailed analysis of their potential adversaries.
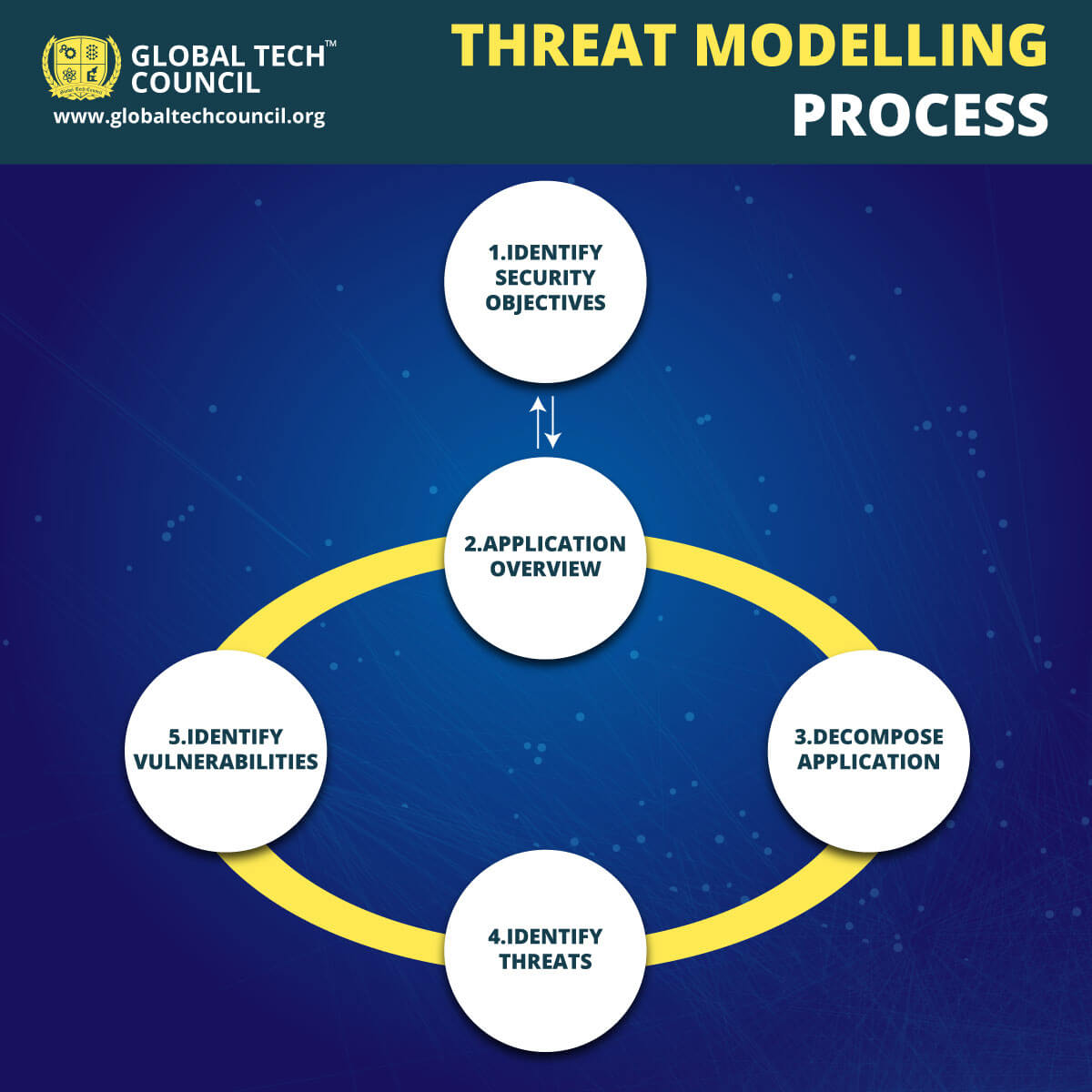
THREAT MODELLING PROCESS
Any cybersecurity training is incomplete without this. The steps can be explained as :
BENEFITS OF THREAT MODELLING
Threat modeling has a lot of benefits for the security of the organization. Not only has it ensured safety today, but also for the future.
-
Optimized Risk profile
It leads to the creation of an updated and accurate risk profile. The information can be used for audits and for implementing security guidelines.
-
Security Policy
Enterprise-wide promotion of consistent security policy, i.e., having a comprehensive repository of threat data, promotes security consistency.
-
Mitigation Strategy
The associated costs can be aligned and prioritized with mitigation efforts. Moreover, continuous threat modeling can be used for development for data models.
-
Measure Security
Security is turned into a measurable metric. This can be used in various data analysis techniques to predict trends.
THREAT MODELING METHODOLOGIES
- OCTAVE – Focused on assessing organizational (non-technical) risks that may result from breached information assets.
- PASTA: risk-focused approach: Process for Attack Simulation and Threat Analysis.
- STRIDE (Uses application-centric approach)
- Spoofing of user identity
- Tampering
- Repudiation
- Information disclosure (data leak or privacy breach)
- Denial of service (DoS)
- Elevation of privilege
- TRIKE – Risk-based approach with the risk-modeling process and unique implementation.
- VAST – Visual, Agile and Simple Threat modeling.
TOOLS FOR THREAT MODELING
- Microsoft TMT 2016, a limited solution tool that is used by enterprises. It is based on the STRIDE methodology. It is available free of cost.
- ThreatModeleris based on VAST methodology. It is for modern and agile DevOps teams. It also supports operational threat modeling.
- OWASP Threat Dragon: It comes in two variants, i.e., an online web application for GitHub and second an installable desktop application.
TRENDS IN CYBERSECURITY
- The unemployment rate of cybersecurity is at zero percent.
- Huge demand for cybersecurity experts in the industry, due to cyber talent crunch.
- Individuals advised to take up cybersecurity training online to develop the required skills.
- Moreover, recognized cybersecurity certifications are being promoted vigorously.
- Readers Digest named cybersecurity experts and blockchain developers on its list of the 21 most in-demand jobs for 2020.
Conclusion
Threat modeling is very crucial for a cybersecurity strategy. Moreover, any cybersecurity training online is incomplete without threat modeling. If you want to learn more or want to have some hands-on exposure, you can sign up for Cyber Security Certification online.
This can help you to develop the required skills to become a cybersecurity expert.
Leave a Reply